Importance of Role Design in SAP Security
As a security consultant engaged in the blueprinting phase of an SAP Implementation project, you are tasked with discussing the SAP role design and authorization provisioning strategy with your multinational client organization.
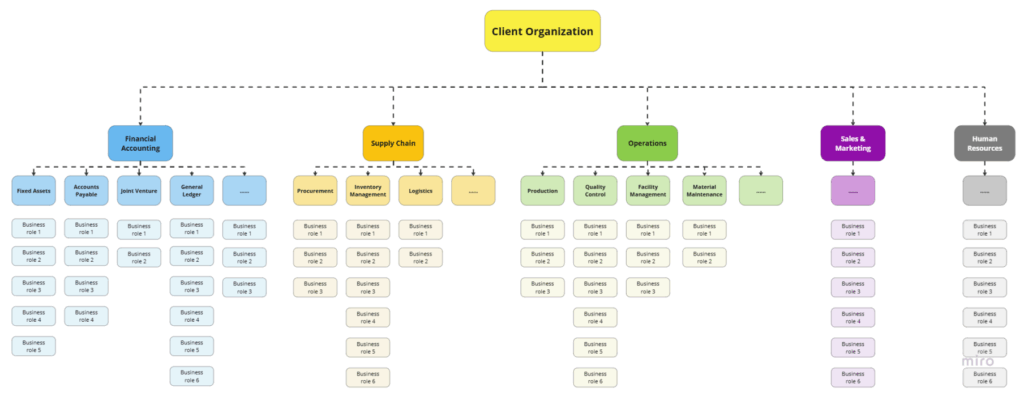
The organization’s structure consists of 5 to 6 distinct process areas, including Financial Accounting, Operations, Supply Chain, Sales and Marketing, and others. Each process area encompasses 5 to 10 sub-processes (for example, Finance includes Fixed Assets, Accounts Payable, and Accounts Receivable; Supply Chain includes Logistics, Inventory, and Procurement). Within each sub-process, employees hold various positions, fulfilling different business roles and responsibilities. Additionally, the organization operates across five global geographical locations.
Considering the need to maintain data integrity and ensure scalable role management for the future, what would be the most efficient and sustainable approach to design and provision SAP roles for this multinational organization?
SAP Master-Derived Role Design Methodology
The Master-Derived role design methodology is an approach to role design where individual roles, referred to as derived or child roles in the backend, inherit authorizations and characteristics from a central role, known as the master or parent role. This methodology facilitates streamlined management where the master role serves as the foundation, and the derived roles automatically adopt authorizations based on the master role’s configuration.
Some Necessary SAP Definitions
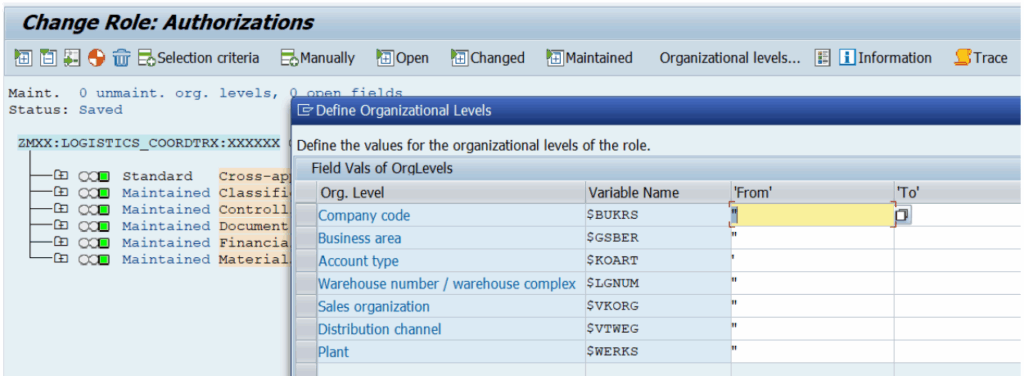
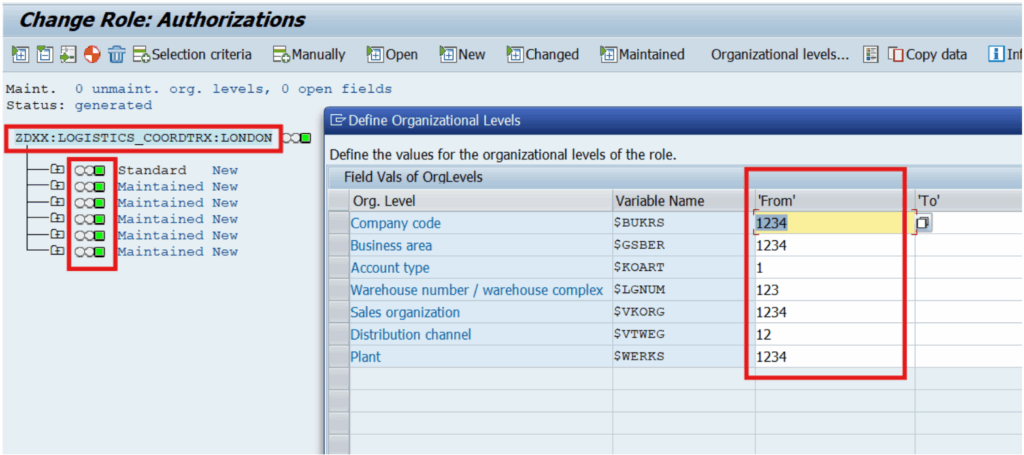
- Master Role: Also called the “Parent role”, a master role is a single role with defined authorizations that is designated to be derived from. Care must be talent to use appropriate and consistent nomenclature to separate the master roles from other single roles (enabler roles, roles meant for a particular infrequent function, etc). The organizational data fields (that control access to organizational data, specific to a geographical location) for the master roles are to be maintained according to the client’s discretion. Best practice dictates that dummy values be maintained to prohibit access to any unnecessary organizational data for every new derived role instance.
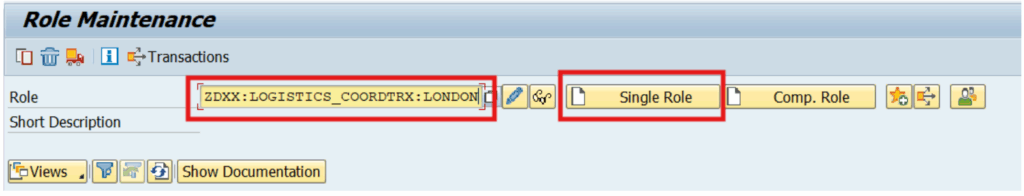
- Derived Role: Also called the “Child role”, a derived role is a single role that inherits its authorizations and organizational values from a master role. Once inherited, the organizational value fields of the derived role can be modified based on the client’s organizational structure. The authorizations in a derived role are typically managed through the master role, which means that any changes required in the derived role must first be made to the master role and then pushed to its derived roles.
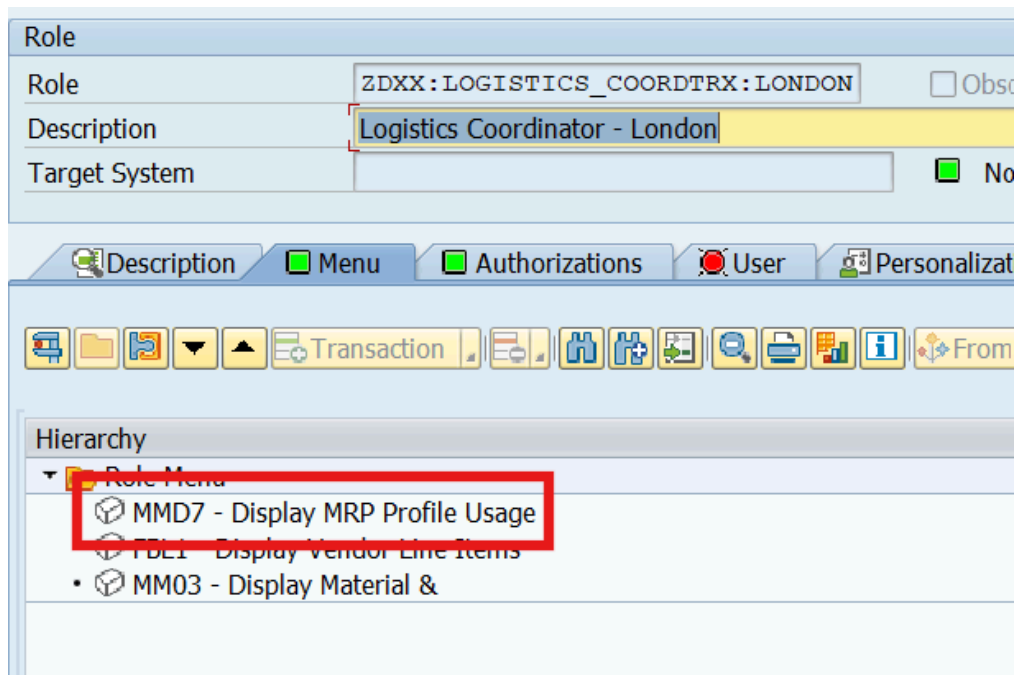
For example, let’s say the client has decided to require its Logistics Coordinators across all locations to submit weekly reports on the inventory status of a specific class of materials. This new responsibility involves granting access to a particular Materials Management (MM) transaction code (t-code).
If the logistics coordinator roles for each geographic location were managed independently, the MM t-code would need to be added to the menu of each role individually. Additionally, the authorizations associated with this t-code would have to be maintained for each role separately, increasing the likelihood of errors. This approach would be repetitive, time-consuming, and inefficient.
With the Master-Derived role design approach, the MM t-code would be added to the Logistics Coordinator master role. Once the required authorizations are updated in the master role, these changes are automatically applied to all derived instances of the Logistics Coordinator role (corresponding to various geographic regions), ensuring consistency and streamlining the role management process.
1) SAP Master Role Creation
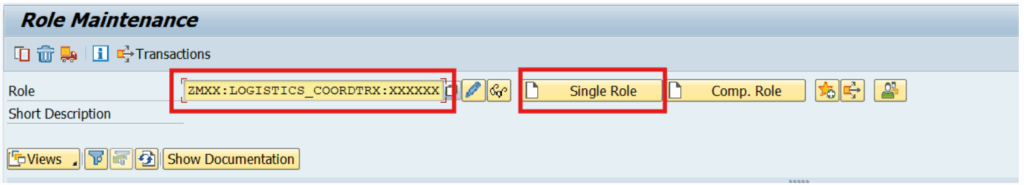
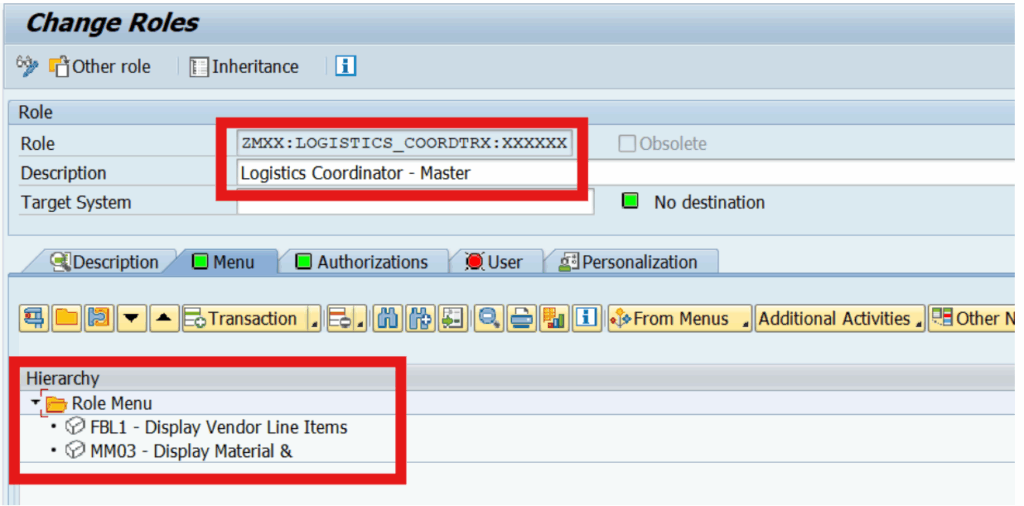
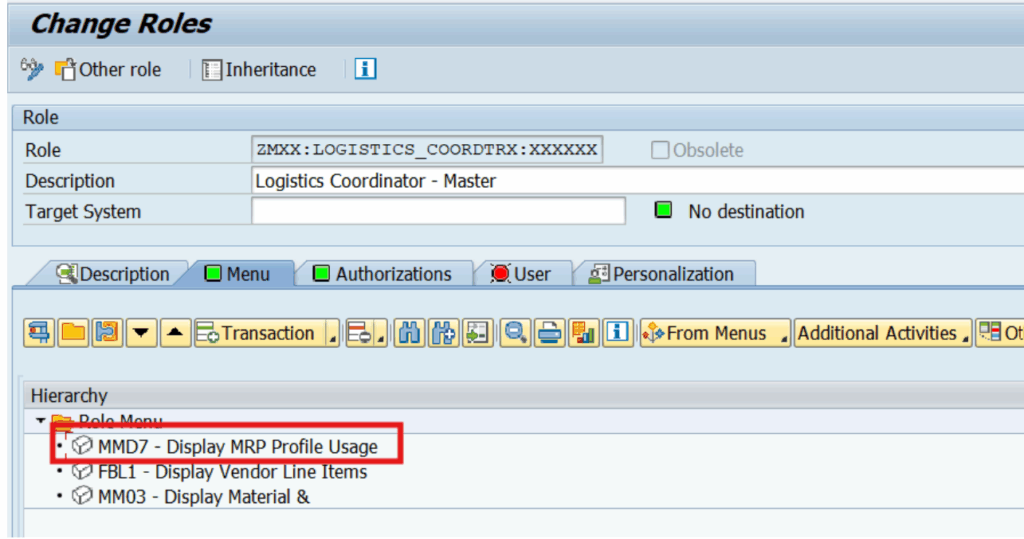
2) SAP Derived Role Creation
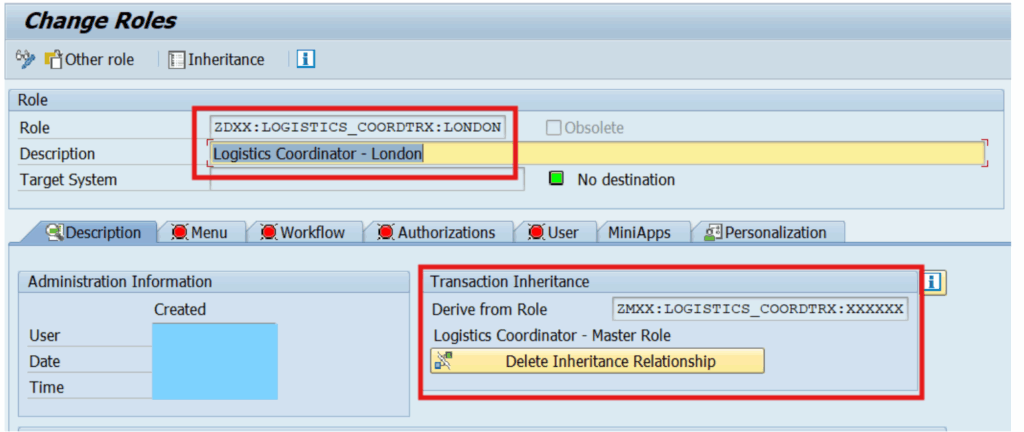
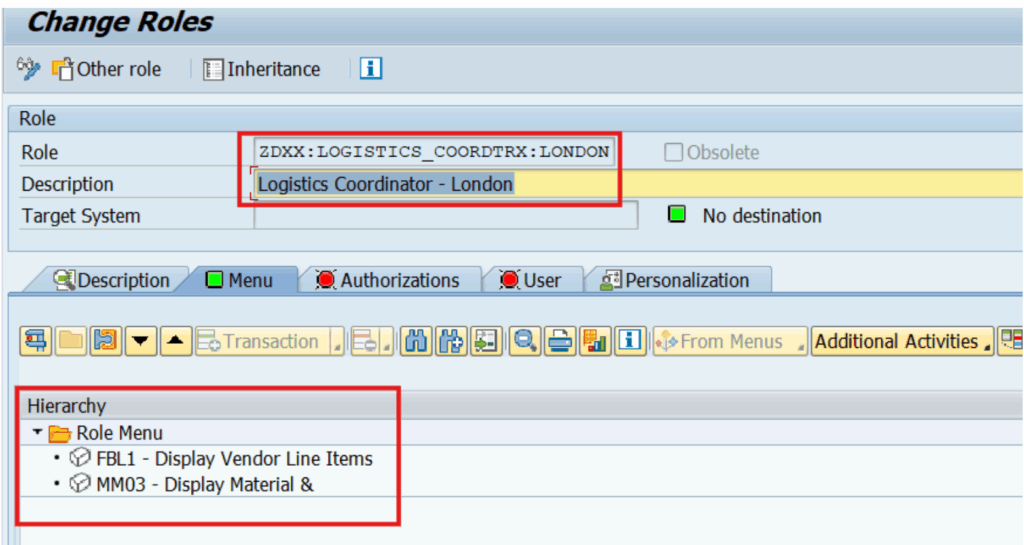
Any role corrections that are to be made to Logistics coordinators across locations can also be administered just through the master role and pushed to the instances of the Logistics Coordinators derived from the master role.
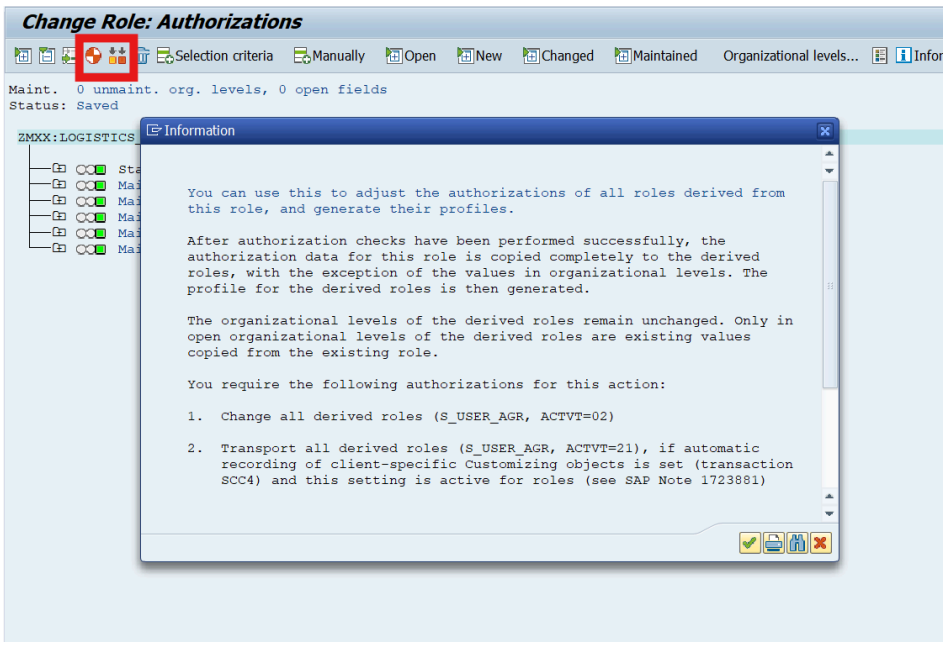
Advantages of the SAP Master-Derived Role Design Approach
- Centralized Role Management: The Master-Derived role approach allows for centralized management of authorizations. Changes or updates to roles, such as adding a new T-code or adjusting authorizations, can be made in the master role and automatically pushed to its derived roles. This streamlines maintenance and ensures consistency across roles for different geographic regions.
- Reduced Risk of Errors: Managing roles individually for each geographical location or sub-process area can lead to errors due to manual handling of multiple instances. With the Master-Derived approach, the authorizations are defined centrally in the master role, significantly reducing the chances of errors.
- Scalability and Flexibility: As the organization expands or introduces new business processes or locations, the Master-Derived role model provides scalability. New derived roles can be created easily from the master role, inheriting the necessary authorizations, and modified as needed based on local data, all without starting from scratch.
- Efficient Role Provisioning: Instead of adding or modifying roles manually for each location or sub-process area, the Master-Derived design enables quicker provisioning of roles. Once the master role is configured, derived roles for different locations or business functions can be created and modified efficiently, making the role provisioning process much faster.
- Consistency Across Global Operations: Since the master role serves as the template for all derived roles, it ensures that roles are consistent across the global organization
SAP Security Architecture
Implementing a Master-Derived Role Design methodology is not just a technical decision—it’s a strategic move toward scalable, secure, and efficient SAP role management. By centralizing control and streamlining provisioning, organizations can reduce errors, maintain consistency, and adapt quickly to evolving business needs. This approach lays the foundation for long-term success in SAP security architecture.
Author Ashwin Jagdish