SAP Segregation of Duties (SoD)
In any large enterprise, Segregation of Duties (SoD) is one of the most important controls to ensure both compliance and operational integrity. It’s a safeguard against fraud, error, and misuse of access. This article explores what SoD risk means, how it arises, its consequences, and how SAP GRC Access Control 12.0 helps manage it.
What is Segregation of Duties (SoD) Risk in SAP?
At its simplest, SoD means that no single individual should have excessive access that allows them to perform conflicting business functions. By separating responsibilities, organizations reduce the risk of fraud, error, and misuse of critical systems. For instance, if an SAP user can both create a vendor (XK01) and make payments (F110), they could create a fake vendor and pay themselves.
SoD risks are not simply about fraud; they also involve unintentional errors. A user with conflicting access may make mistakes that go undetected because they have the ability to both initiate and approve processes.
Why Does SoD Risk Arise in SAP?
SoD risks typically arise from the way roles and authorizations are designed in SAP. Some common reasons include:
- Overlapping responsibilities: Users wear multiple hats, especially in smaller teams.
- Poor role design: Technical roles are built without considering functional conflicts.
- Emergency access or firefighter IDs: Temporary access isn’t revoked properly.
- Business changes: Mergers, reorganizations, or system changes can leave outdated access in place.
Consequences of SoD Risks in SAP
Unchecked SoD risks can lead to significant consequences:
- Fraud and financial loss – A user could manipulate records and conceal their own actions.
- Reputational damage – Stakeholders lose trust if internal controls fail.
- Audit findings and penalties – Regulators may impose fines or restrictions.
- Operational inefficiency – Detecting and correcting misuse consumes time and resources.
A famous example, although not directly SAP-related, is the collapse of Lehman Brothers in 2008. Its downfall highlighted how unchecked risk and lack of controls can bring down even the largest institutions. In the aftermath, lawmakers strengthened compliance requirements, most notably through the Sarbanes-Oxley (SOX) Act of 2002, which had already been established after earlier scandals like Enron. SOX mandates strict internal controls, including proper SoD, to ensure financial integrity and accountability.
SAP GRC Access Control and SoD
SAP Governance, Risk, and Compliance (GRC) Access Control 12.0 provides the framework to identify, analyze, and remediate SoD risks systematically. Its Access Risk Analysis (ARA) module is central to this effort. Let’s break down the core concepts:
- Rule Sets: A predefined library of SoD risks. SAP delivers a global rule set that organizations can adapt to their business processes.
- Business Processes: High-level categories like Procure to Pay, Order to Cash, Hire to Retire, or Record to Report.
- Functions: Specific capabilities within processes, such as “Maintain Vendor Master” or “Post Vendor Payment.”
- Action: An action is a specific transaction that a user can perform in SAP.
- Permission: A permission defines what actions a user is allowed to perform in SAP. Permissions can specify conditions or constraints.
- Rule IDs: Unique identifiers assigned to each SoD rule for tracking and reporting.
Risk Definition: A documented description of why a combination of functions poses a risk (e.g., “Ability to both create and pay a vendor”).
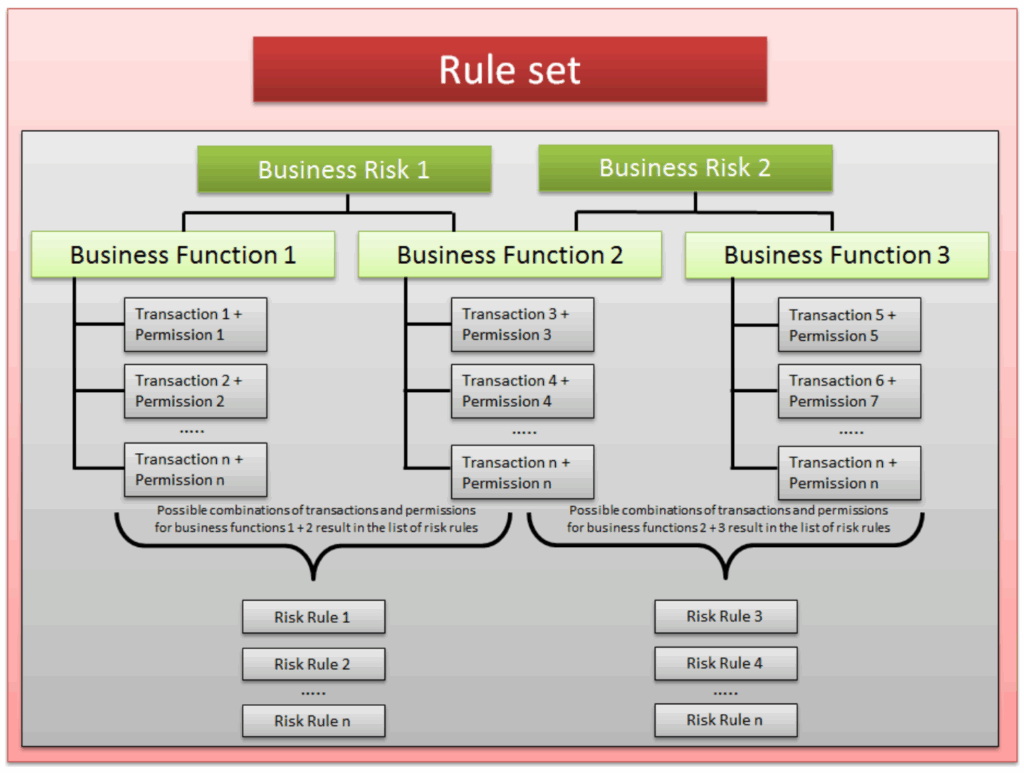
SoD risk in Business Context
In accordance with the example discussed, for the Procure to Pay (P2P) process, one defined function is Vendor Master Maintenance, and another is Vendor Payment Processing.
Each function is made up of actions, which are the underlying SAP tcodes. The Vendor Master Maintenance function includes XK01 (create vendor) and XK02 (change vendor), while the Vendor Payment Processing function includes F110 (automatic payment run). These tcodes represent the permissions a user has in the system.
Individually, each function is valid: one team maintains vendor records, and another processes payments. But if a single user has both functions, the rule set identifies a conflict. In GRC, this might be recorded under a Rule ID, for instance P2P_001, with the risk definition stating: “Users can create or modify vendor data and execute payments, enabling potential fraudulent activity.” Because this allows the same person to both set up and pay a vendor, the risk is classified as “High”. The risk owner, usually the P2P process owner, is responsible for ensuring the conflict is either remediated (restructuring roles) or mitigated (workflow approvals and monitoring reports).
SAP Risk Mitigation
Not all SoD risks can be eliminated. Some access conflicts may be necessary for certain roles. In these cases, mitigation controls are applied. These include measures like:
- Independent monitoring reports reviewed periodically.
- Manual approvals by a different person for sensitive transactions.
- Workflow-based approvals in SAP.
- Mitigation activities are documented and linked to the risk in GRC for transparency.
SAP Role-Levels and User-Level Risk Analysis
Role-level analysis checks if a role, in its design, carries conflicting access. For example, a custom role may include both vendor maintenance and payment transactions. Fixing this early prevents conflicts from spreading.
User-level analysis checks the combination of all roles assigned to a user. A user might not have conflicts within a single role, but when two or more roles are combined, an SoD violation may appear.
SAP GRC provides simulation tools where security consultants can run “what-if” analyses before assigning roles, ensuring clean user provisioning.
GRC Access Control 12.0
Segregation of Duties is more than just a checkbox for compliance—it is a cornerstone of trustworthy enterprise operations. The collapse of institutions like Lehman Brothers reinforced the importance of strong governance frameworks, while SOX codified the need for internal controls. In SAP environments, GRC Access Control 12.0 empowers organizations to detect, remediate, and monitor SoD risks effectively.
By understanding rule sets, risk definitions, mitigation strategies, and the difference between role-level and user-level analyses, SAP Security Consultants ensure that organizations not only stay compliant but also protect their integrity and resilience in the long run.
Author Ashwin Jagdish

