
by Joe Markgraf | Aug 1, 2025 | GRC, SAP
SAP Super Role Assignments In SAP environments, access to Production systems must be strictly monitored. This article will discuss an audit that should be performed frequently to manage Super Role assignments with precision. This blog will break down the purpose,...

by Danny Shafer | Jun 30, 2025 | SAP
Why Archive Data in SAP? In today’s data-driven business environment, SAP systems accumulate vast volumes of transactional and master data over time. Without proper data management, system performance can degrade, backups become slower, and storage costs increase...
by Joe Markgraf | Feb 25, 2025 | SAP
SAP Access Controls: Emergency Access Management (EAM) Emergency Access Management (EAM) in SAP Access Control allows for the definition, management, and monitoring of emergency access. It enables users to take on tasks outside their normal roles by granting temporary...

by Danny Shafer | Jan 22, 2025 | SAP
Have you experienced issues in the past with overflowing log files, difficulties deleting backups, or concerns that there is unwanted data affecting performance in your database? HANA Cleaners is an effective tool with the main goal of alleviating those concerns and...
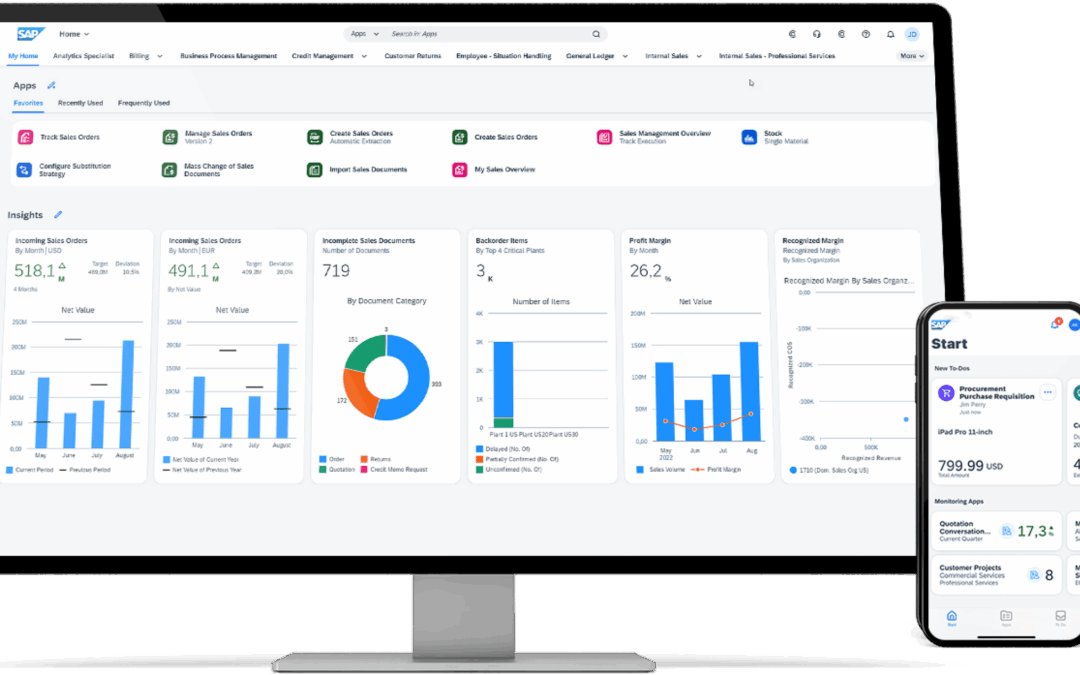
by Joe Markgraf | Jan 7, 2025 | SAP
What’s New in SAP Fiori As organizations continue to modernize their SAP environments, user experience and system performance have become critical priorities. One area that has seen significant evolution is the SAP Fiori launchpad layout. Traditionally, the Groups...

by Joe Markgraf | Dec 17, 2024 | GRC, SAP
SAP GRC Access Control Access control is a fundamental aspect of Governance, Risk Management, and Compliance (GRC) that protects sensitive organizational data and systems from unauthorized access. As the digital landscape grows increasingly complex, mastering GRC...







